Free Coaching Lectures - Free NEET and AIIMS Coaching Lectures | Free Medical Entrance Coaching Lectures | Free CBSE Board Coaching Lectures | Free Biology Coaching Lectures | Free Physics Coaching Lectures | Free Chemistry Coaching Lectures | www.ConceptsMadeEasy.com

Use this Coupon to get upto 70% OFF on Hostarmada Affordable Cloud SSD Web Hosting Services
Following are the list of best awaresome videos on "W0jsxcha') Or 153=(select 153 From Pg_sleep(15))" which you can watch online here or download.
 Blind SQL Injection Made Easy
Blind SQL Injection Made Easy
00:00 Intro 01:12 Snyk Ad 02:31 Blind SQLi Primer 03:55 Hands-on lab 11:30 Outro Pentests & Security Consulting: ... DOWNLOAD
 SQL Injections Explained - The #1 Way Websites Are Hacked
SQL Injections Explained - The #1 Way Websites Are Hacked
Learn Full Stack Development on codedamn: https://cdm.sh/fullstack Timestamps 0:00 Teaser 0:34 Video Starts 2:35 How SQL ... DOWNLOAD
 What is SQL injection? - Web Security Academy
What is SQL injection? - Web Security Academy
SQL injection is a web security vulnerability that allows an attacker to interfere with the queries that an application makes to its ... DOWNLOAD
 Sql Injection Explained by Example with Express and PostgreSQL
Sql Injection Explained by Example with Express and PostgreSQL
More Software engineering videos https://www.youtube.com/playlist?list=PLQnljOFTspQXOkIpdwjsMlVqkIffdqZ2K Sql injection is ... DOWNLOAD
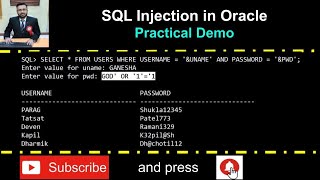 SQL Injection in Oracle with Practical Demo
SQL Injection in Oracle with Practical Demo
Warning: Purpose of this video is to demonstrate SQL Injection practically and it is for education purpose only. It is strongly ... DOWNLOAD
 SQL Injection - Lab #11 Blind SQL injection with conditional responses
SQL Injection - Lab #11 Blind SQL injection with conditional responses
In this video, we cover Lab #11 in the SQL injection track of the Web Security Academy. This lab contains a blind SQL injection ... DOWNLOAD
 SQL Injection - Lab #2 SQL injection vulnerability allowing login bypass
SQL Injection - Lab #2 SQL injection vulnerability allowing login bypass
In this video, we cover lab #2 in the SQL injection track of the Web Security Academy. This lab contains a SQL injection ... DOWNLOAD
 50 Inband SQL Injection over a Select Form
50 Inband SQL Injection over a Select Form
 SQL Injection - Lab #15 Blind SQL injection with out-of-band interaction
SQL Injection - Lab #15 Blind SQL injection with out-of-band interaction
In this video, we cover Lab #15 in the SQL injection module of the Web Security Academy. This lab contains a blind SQL injection ... DOWNLOAD
 SQL injection attack, querying the database type and version on MySQL and Microsoft
SQL injection attack, querying the database type and version on MySQL and Microsoft
This lab contains an SQL injection vulnerability in the product category filter. You can use a UNION attack to retrieve the results ... DOWNLOAD
 Penetration Testing - SQL Injection
Penetration Testing - SQL Injection
SQL Injection Watch more videos at https://www.tutorialspoint.com/videotutorials/index.htm Lecture By: Mr. Sharad Kumar, ... DOWNLOAD
 PostgreSQL Security Features: Episode 6 - SQL Injection Attacks
PostgreSQL Security Features: Episode 6 - SQL Injection Attacks
An SQL #injection attack is an attempt to compromise a database by running SQL statements that provide clues to the attacker as ... DOWNLOAD
 What is a SQL Injection Attack? - The Complete Python/PostgreSQL Course 2.0.
What is a SQL Injection Attack? - The Complete Python/PostgreSQL Course 2.0.
What is a SQL injection attack? How does it happen? How can you stop it?! Find out now in this lecture from Jose Salvatierra\'s ... DOWNLOAD
 SQL Injection Lab13# Blind SQL Injection with Time Delay - Web Security Academy
SQL Injection Lab13# Blind SQL Injection with Time Delay - Web Security Academy
 UNION SQL Injection to Extract Data From Other Tables!
UNION SQL Injection to Extract Data From Other Tables!
Learn about SQL Injection vulnerabilities. In this video, we are going to have a look at a UNION SELECT query to extract data from ... DOWNLOAD
 list all schemas in a postgresql database using psql and SQL Query postgreSQL 15 pgAdmin 4 tutorial
list all schemas in a postgresql database using psql and SQL Query postgreSQL 15 pgAdmin 4 tutorial
in this video i explain three methods to list all schemas in a postgresql database postgreSQL 15 pgAdmin 4 SQL Query SQL ... DOWNLOAD
 Dangerous Codes: SQLi
Dangerous Codes: SQLi
short #infosec #sql #sqlinjection. DOWNLOAD
 🔥What is SQL Injection || 😱Easiest Way To Hack || Hack2skill #programming #technology #coding
🔥What is SQL Injection || 😱Easiest Way To Hack || Hack2skill #programming #technology #coding
 SQL Injection - Lab #3 SQLi UNION attack determining the number of columns returned by the query
SQL Injection - Lab #3 SQLi UNION attack determining the number of columns returned by the query
In this video, we cover Lab #3 in the SQL injection track of the Web Security Academy. This lab contains a SQL injection ... DOWNLOAD
 SQL Injection : Data Science Code
SQL Injection : Data Science Code
Avoiding the dangers of SQL Injection. DOWNLOAD
 How to perform SQL injection (error based)
How to perform SQL injection (error based)
In this video I explain what is SQL as well as how to perform an SQL injection attack using PortSwiger - Web security academy. DOWNLOAD
 SQL Injection - Lab #11 Blind SQL injection with conditional responses
SQL Injection - Lab #11 Blind SQL injection with conditional responses
In this video, we cover Lab #11 in the SQL injection track of the Web Security Academy. This lab contains a blind SQL injection ... DOWNLOAD
 What is SQL Injection ? How to prevent SQL Injection Attack in php/mysql ?
What is SQL Injection ? How to prevent SQL Injection Attack in php/mysql ?
What is SQL Injection ? It is a technique to attack data driven applications. This attack can bypass a firewall and can affect a fully ... DOWNLOAD